Identify and analyze security gaps with our deep scans that reveal and eliminate every hidden threat.
 Complete Visibility
Complete Visibility Gain 360° visibility into your security operations with reports covering every aspect of your website’s security posture.
 Non-Technical Reports
Non-Technical Reports Get clear security insights without technical terms, Our reports simplify complex data, empowering informed decisions.
 Comprehensive Scanning
Comprehensive Scanning We use standard and deep scans to evaluate your website; deep scans thoroughly examine code for detailed security assessment
Our comprehensive solution for safeguarding your website provides a clear view of your security posture through detailed, accessible reports. We include user-friendly insights to help you address critical vulnerabilities, maintain compliance, and stay informed about ongoing security changes.
Secure Your Website in 4 Simple Steps:

Fill out the form with your website details to initiate the scan.

Our expert team uses advanced technology to conduct a thorough security examination.

Receive detailed reports on vulnerabilities and potential threats detected during the scan.

Get tailored recommendations to address and close identified security gaps effectively.
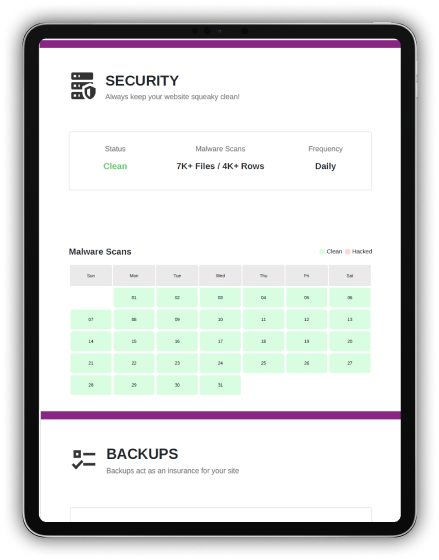
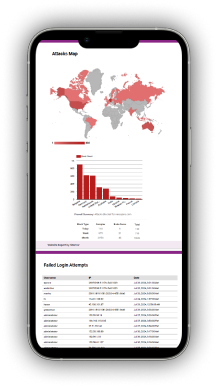
Our reports provide deep Website security analysis, identifying all security gaps and prioritizing risks.
Receive a comprehensive overview with actionable insights to address vulnerabilities and enhance your protection.
Gain a clear view of your website’s security posture and enhance protection.
Start our advanced deep scan to detect and analyze security gaps today.

Typically, you can expect to receive the scan results within One business day. The exact timing may vary depending on the size and complexity of your website.
Absolutely. Along with the report, we provide actionable recommendations for each vulnerability. If you need additional support, our team can assist with remediation efforts or offer guidance on how to fix the issues.
We follow strict data protection protocols to ensure your website’s data remains secure. All data transmitted during the scan is encrypted, and we adhere to industry best practices for data handling and privacy.
We conduct an initial scan first, and if any gaps are identified, we request access to your site with relevant credentials for deeper, more advanced scanning. We'll provide you with a checklist of specific requirements or preparations needed to ensure a smooth scanning process.
If any gaps are identified and your website requires a deep scan, our analysis will cover a wide range of vulnerabilities, including SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), broken authentication, and security misconfigurations. We also evaluate vulnerabilities in third-party components and libraries used on your site.

